前言
在刷mobile题的时候遇见了这道题,在这道题中学到了许多新的东西,特此记录一下,整篇下来真的是手把手,保姆级教学
题目下载:MOIBLE-easyapp
分析程序代码
Java层
下载附件之后查看文件信息发现是一个没有加固的.apk文件,我们用JEB看看:
进入MainActivity之后可以看见:
package com.example.ndktest2;
import android.os.Bundle;
import android.view.View.OnClickListener;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
public class MainActivity extends AppCompatActivity {
private EditText password;
static {
System.loadLibrary("native-lib");
}
public native String Encrypt() {
}
@Override // androidx.appcompat.app.AppCompatActivity
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(0x7F09001C); // layout:activity_main
EditText password = (EditText)this.findViewById(0x7F07005B); // id:password
((Button)this.findViewById(0x7F07004E)).setOnClickListener(new View.OnClickListener() { // id:login
@Override // android.view.View$OnClickListener
public void onClick(View view) {
if(password.getText().toString().equals(MainActivity.this.Encrypt())) {
Toast.makeText(MainActivity.this, "登录成功", 1).show();
return;
}
Toast.makeText(MainActivity.this, "登录失败", 0).show();
}
});
}
}
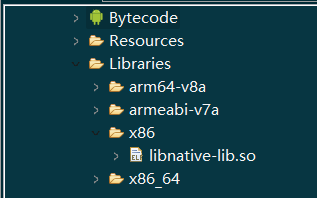
可以看见调用了本地库中的"native-lib",我们可以从Libraries中查看这些本地库文件
其中public native String Encrypt()使用了.so文件中的Encrypt()函数来加密flag,我们使用IDA导入libnative-lib.so文件查看一下这个函数
native层
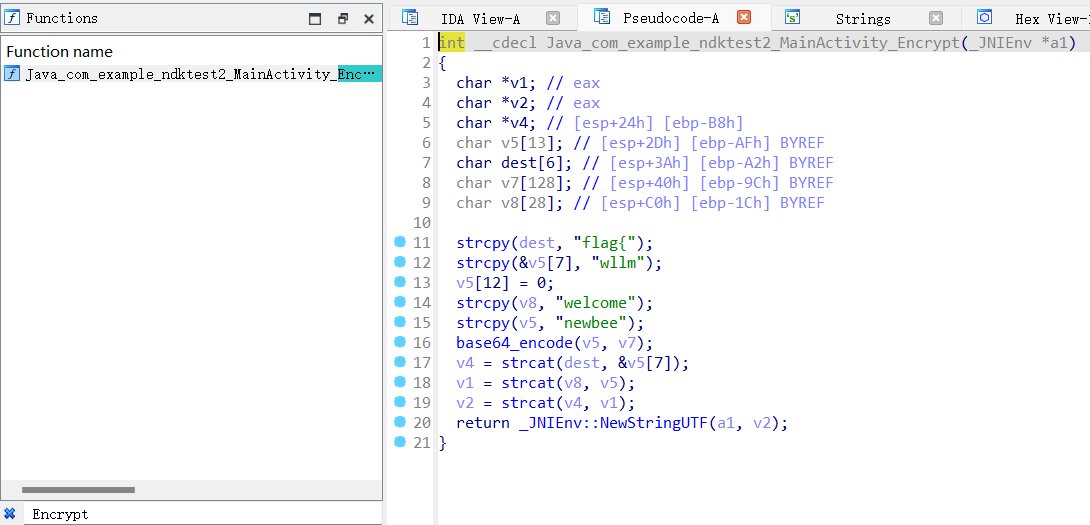
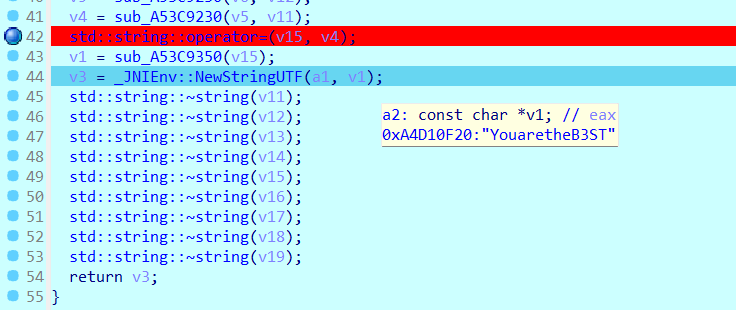
可以看见只有一个函数,我们直接进去就可以了
当时以为是一个base64加密,传入参数v5也就是上面的一些字符串进行base64加密,参数v7是base64码表,函数的返回值就是编码结果。然后返回值与flag{wllmwelcome拼接就是结果了
结果发现还没跑到断点处就登录失败了,想想别的办法吧
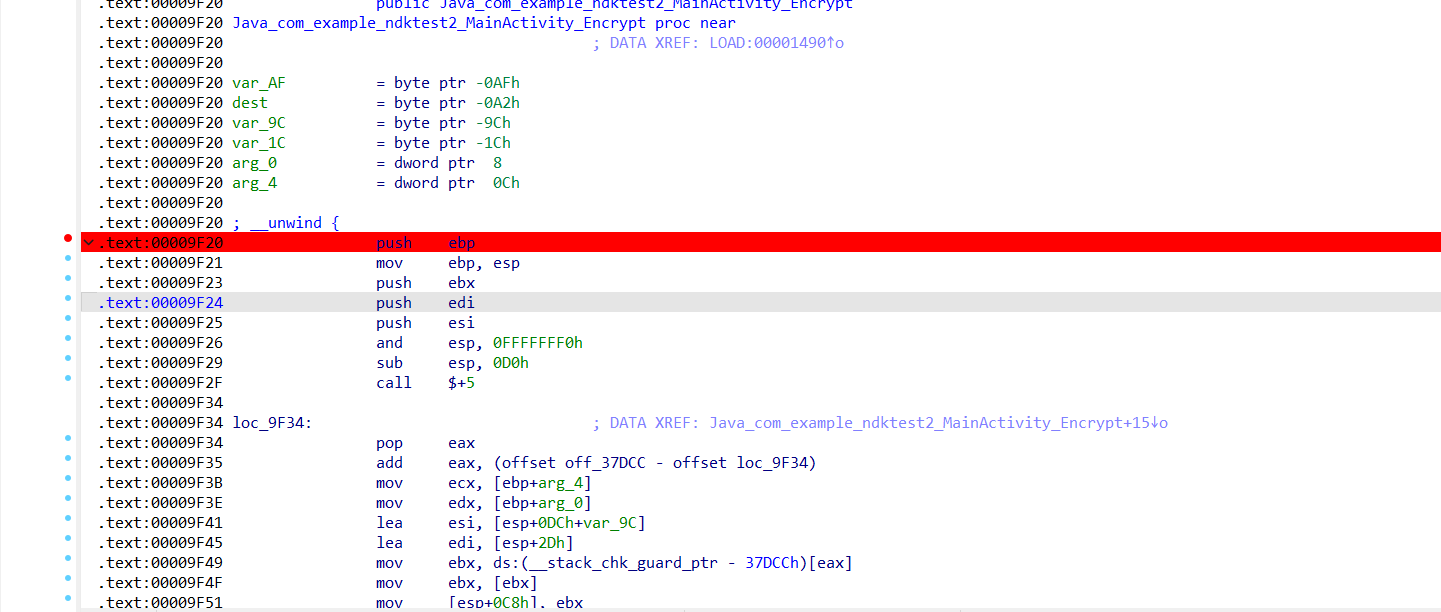
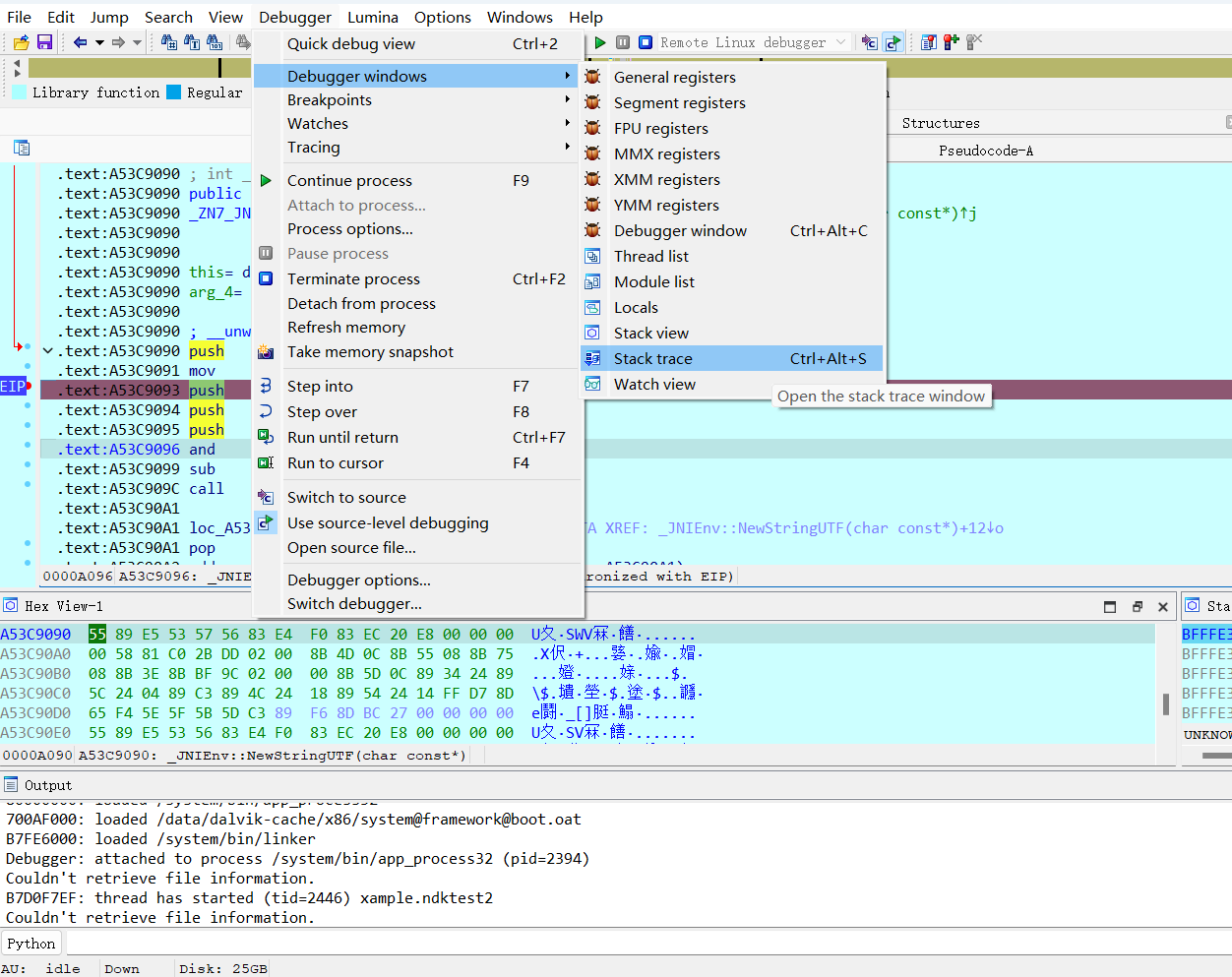
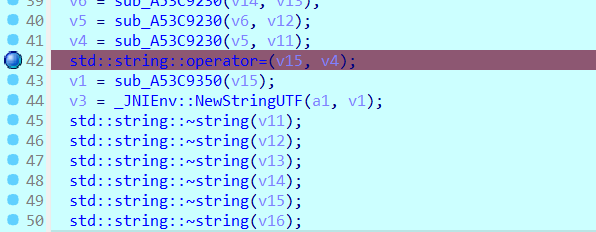
后面通过了解,知道了NewStringUTF 是一个JNI函数,用于将本地的C或C++字符串转换为Java的UTF-8字符串,这个函数在真正的加密函数之中肯定也会被用到的,而假的加密函数Encrypt中也调用了这个函数,所以我们去这个函数下断点
断点下在:A53C9093,因为push ebp;mov ebp, esp;要保存栈帧
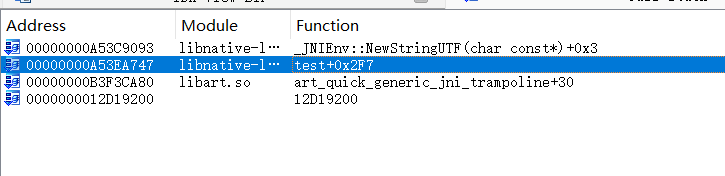
跑一下发现跑起来了,这说明并没有反调试,而是加密函数被混淆了或者被hook了,我们可以通过函数调用栈找到真正的加密函数
所谓函数调用栈就是当我们每一个函数被调用时,都会在出栈入栈时留下自己的足迹,在寄存器ebp中。于是我们就可以通过函数调用栈找到哪一个函数偷偷调用了这个字符串处理函数
关于函数栈帧:【详解】函数栈帧——多图(c语言)指针与函数值传递-CSDN博客
最终找到真正的加密函数是test
进一步探究函数是如何被混淆的
作为一名逆向工程爱好者,最好具有一颗能够深入探究的好奇心,这对我们是非常有好处的。因此我将继续探究函数是如何被混淆的,而不是得到了flag就匆匆了事
找到一篇有关这个题的wp,有关这个题的wp真的很少(相对于其他题目来说),而且大部分的解法是用Frida去hook
第十届SWPUCTFwriteup-安全客 - 安全资讯平台 (anquanke.com)
这个wp其中讲到了与JNI_OnLoad有关
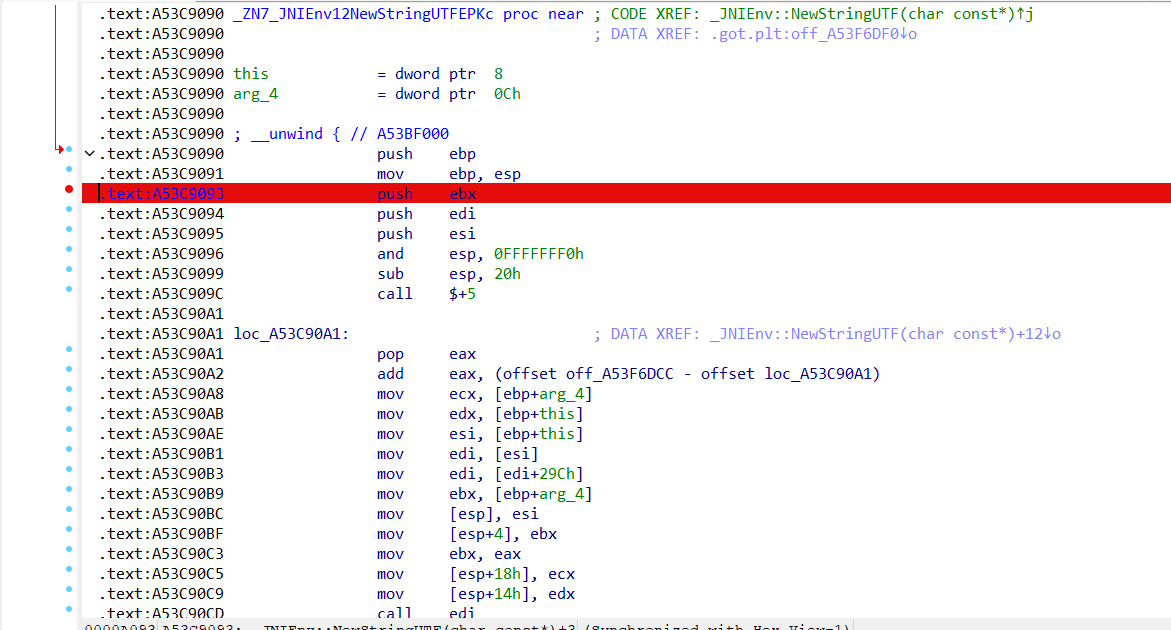
我们通过函数搜索窗口进入JNI_OnLoad函数去看一下
int __cdecl JNI_OnLoad(_JavaVM *a1)
{
void *v3; // [esp+24h] [ebp-18h] BYREF
if ( _JavaVM::GetEnv(a1, &v3, 65542) )
return -1;
if ( sub_A570(v3) )
return 65542;
return -1;
}进入下面的sub_A570函数:
_BOOL4 __cdecl sub_A570(_JNIEnv *a1)
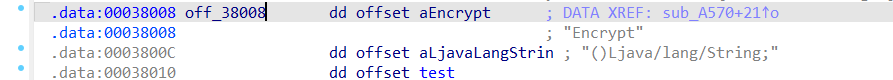
{
return sub_A5F0(a1, "com/example/ndktest2/MainActivity", off_38008, 1) != 0;
}发现涉及了MainActivity,再进入sub_A5F0函数去,在此之前先看看这篇JNI 学习笔记——通过RegisterNatives注册原生方法 - 简书 (jianshu.com)
_BOOL4 __cdecl sub_A5F0(_JNIEnv *a1, char *a2, int a3, int a4)
{
int Class; // [esp+24h] [ebp-18h]
Class = _JNIEnv::FindClass(a1, a2);
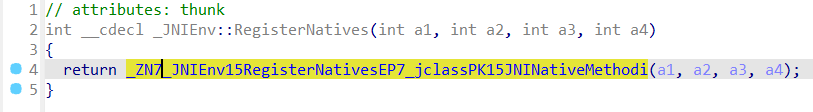
return Class && _JNIEnv::RegisterNatives(a1, Class, a3, a4) >= 0;
}找到了RegisterNatives,注册native
再进入RegisterNatives,发现返回了JNINAtiveMethod,这是一个结构体
JNINativeMethod 结构体数组用于在JNI中注册本地方法。不得不说,注册的过程与WindowsAPI有些许异曲同工之妙
其结构体包含以下字段:
`char* name` 本地方法
`char* signature` 签名
`void* fnPtr` 实际的本地函数我们回到RegisterNatives的上级函数sub_A570,发现它的返回函数sub_A5F0即RegisterNatives其中的参数中的off_38008正好符合上述的结构体:
其中 getNativeString 为Java类中定义的Native方法名。
()Ljava/lang/String; 为方法的签名, () 表示该方法无参数, Ljava/lang/String; 表示返回值为
Java中的String类型。
所以Encrypt函数只是本地方法,实际上的本地函数即真正的加密函数就是test函数
解法一:动态调试.so文件
准备工作
本次学习动调.so文件主要来源是:
adb查看手机设备型号、品牌、机型等信息_abd 获取手机型号-CSDN博客
Frida安装与使用,对nu1lbook第四章-数字壳的传说题目进行脱壳_数字壳 frida-CSDN博客
以及学长的手把手教学)
本次用到的设备是:雷电模拟器、JEB4.20.0、IDA Pro 8.3、Windows、ADB
这里需要注意,由于题目文件过于老旧,需要安卓5及以下的安卓手机/模拟器,否则程序会由于不适配而崩溃!当时我这里卡了很久,结果发现是版本的问题.。。
搭建模拟器与IDA之间的桥梁
首先启动模拟器,同时将APK文件安装进模拟器
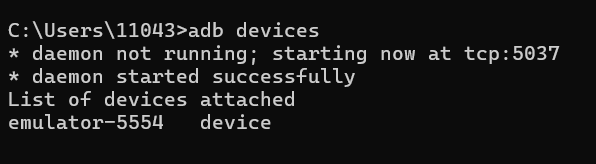
再打开Windows的终端,cmd和powershell都可以,输入adb devices查看有几个手机设备:
只有一个设备被搜索到,端口是5037,但是因为只有一个设备端口就不用管了
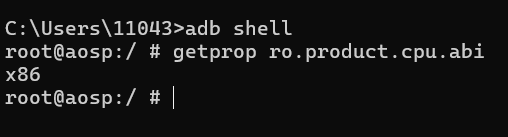
输入adb shell连接到手机,再输入getprop ro.product.cpu.abi查看手机型号:
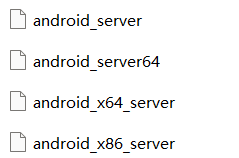
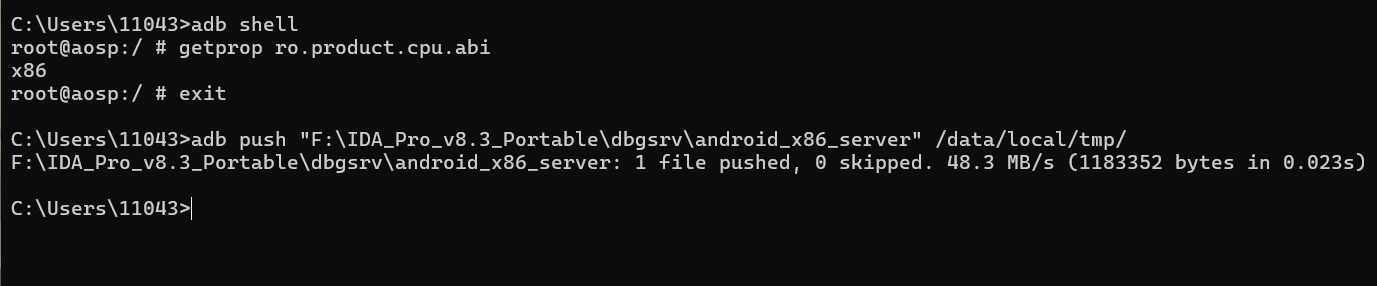
知道是x86的架构之后我们就可以把IDA中对应的server push进模拟器了
前两个server是arm架构的,我们需要用到的是后面的x86架构
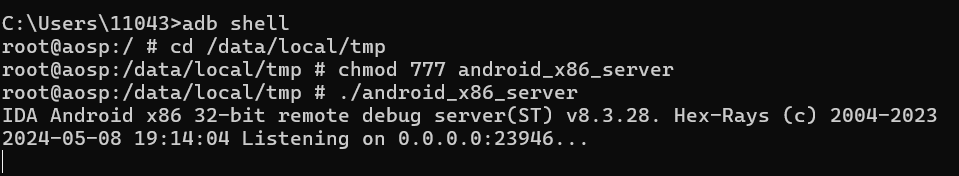
输入exit退出adb shell模式,将android_x86_serverpush进模拟器中:
再次进入adb shell模式,cd到server所在的目录给予文件权限,然后运行:
如图所示就算是运行成功了
再重新打开另一个cmd,将模拟器的端口转发到电脑,若不执行此步骤,可能会导致使用IDA调试时无法连接到模拟器:
使用JEB启动调试
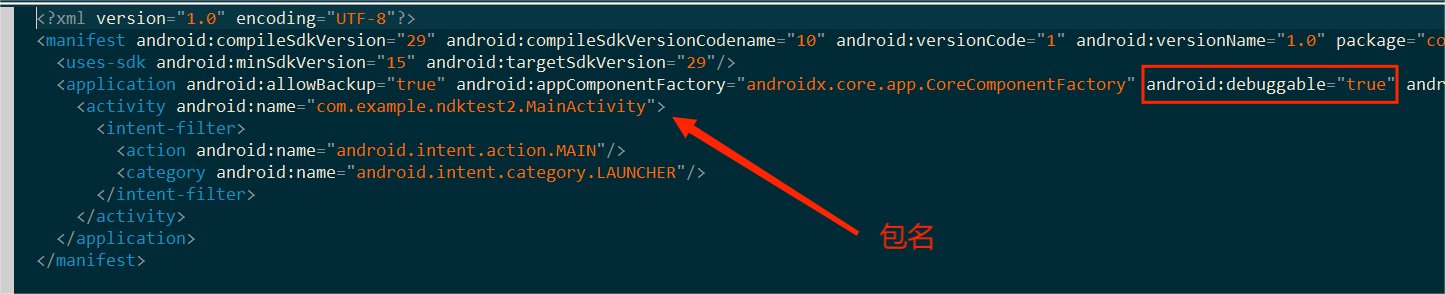
首先打开JEB导入apk文件,在manifest看是否有调试权限
这里显示的是true就表示有文件调试权限,同时我们还可以找到包名:
<activity android:name="com.example.ndktest2.MainActivity">
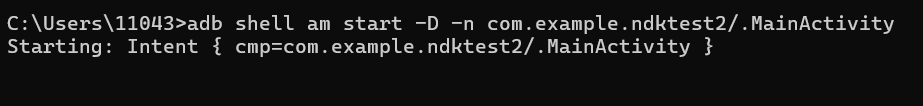
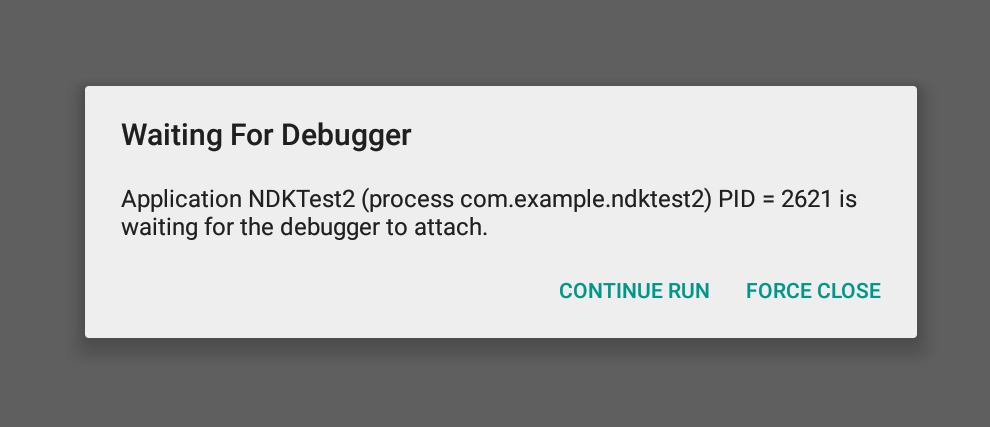
在cmd中启动调试:输入命令adb shell am start -D -n com.example.ndktest2/.MainActivity
这就算是启动成功了,我们可以在模拟器中看见等待调试的页面:
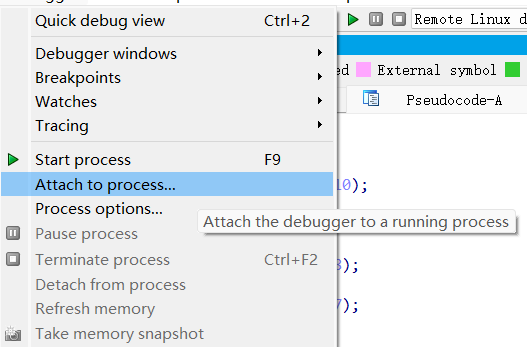
这时我们就可用JEB启动app调试了,在debugger窗口点击开始
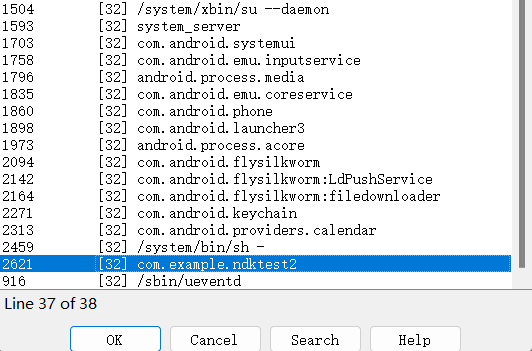
双击下面的进程就可以启动了,我们就会在模拟器中看见程序正常运行
在IDA中调试.so文件
在完成上述步骤之后,我们就已经完成了使用IDA Pro调试.so文件的所有前置准备工作了
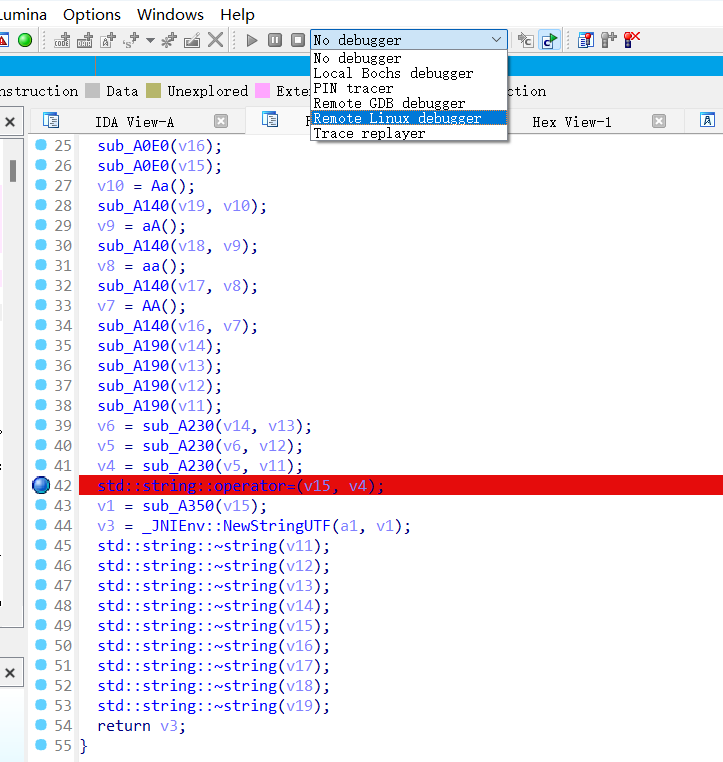
在IDA中打开,在加密函数处下断点:
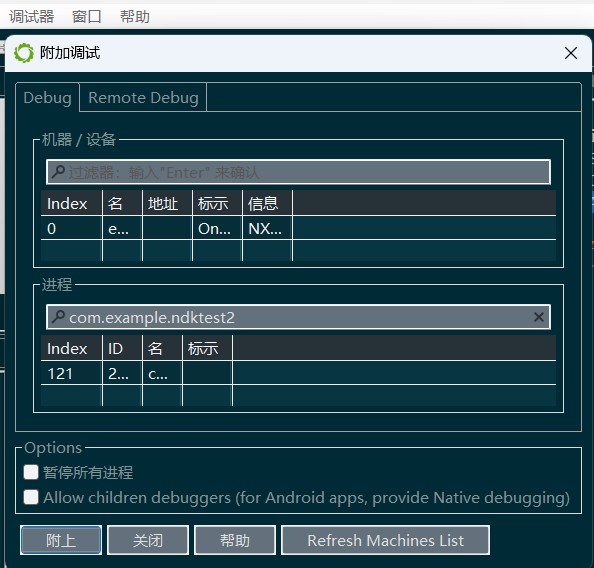
点击Remote Linux debugger模式
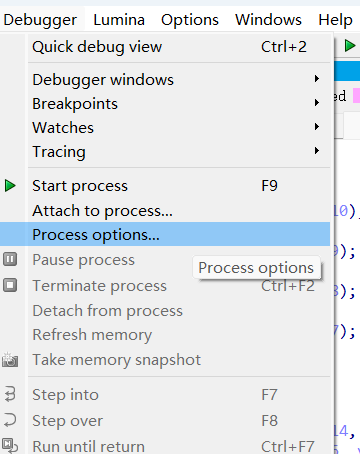
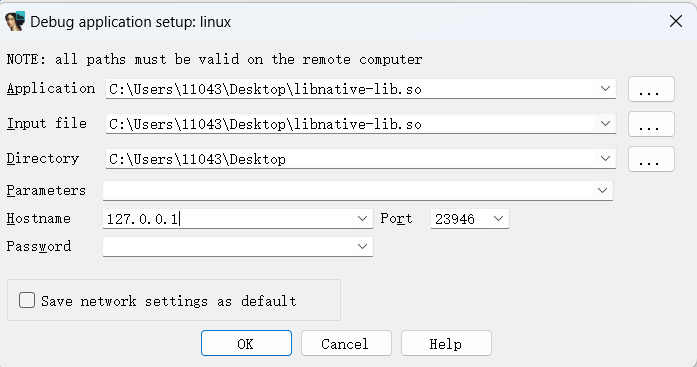
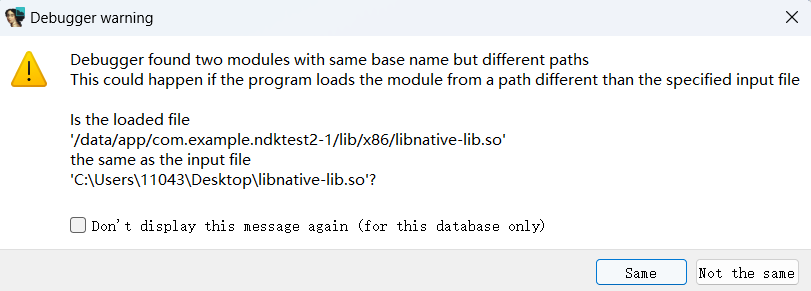
点击debugger窗口中的Process options:
我们点击Same就可以进入调试了
点击登录,IDA就会运行到断点处,就跟我们平常使用IDA进行本地调试一样
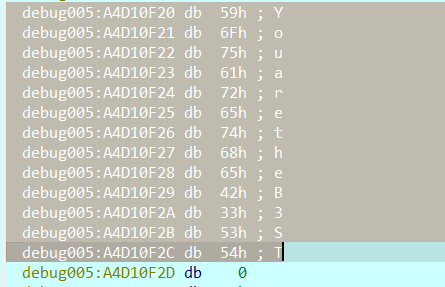
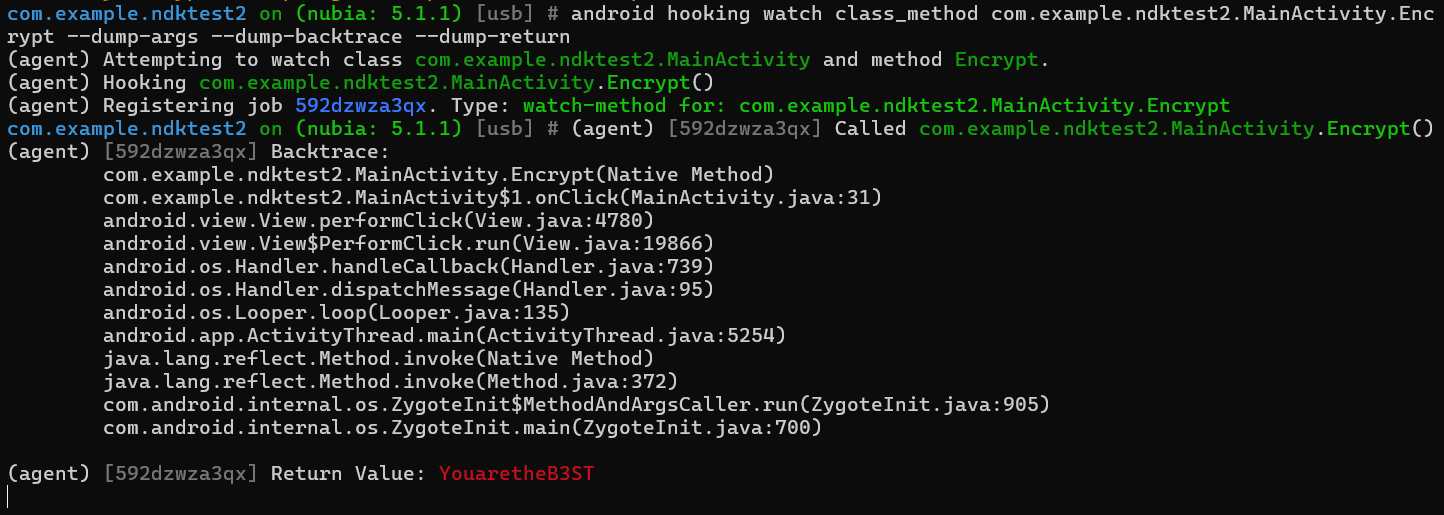
提取出来就获取到flag了:YouaretheB3ST
解法二:使用Frida去hook函数
准备工作
我们在面对不同版本的安卓环境时有不同的Frida版本更适配,比如Android 8.1 适合Frida12.8.X 系列的,Android 10 适合Frida 14以上的,那么不断的重复安装是没有效率的事情,所以需要能简单管理多个Python环境的工具。常见的python管理工具有pyenv、virtualenvwrapper、anaconda、miniconda等,但其中也有一些不太适合在Windows系统上安装和使用,本次我使用的是anaconda
anaconda的安装和使用(管理python环境看这一篇就够了)-CSDN博客
官网下载地址:https://www.anaconda.com/download
下载之后跟着安装就行了,一路next,可以自定义安装路径的,不用安在C盘
安装合适的python环境
装好anaconda之后我们可以在win中找到终端,我们进入anaconda的终端:
可以先查看目前python版本:
(base) C:\Users\11043>conda info
active environment : base
active env location : F:\Anaconda
shell level : 1
user config file : C:\Users\11043\.condarc
populated config files : C:\Users\11043\.condarc
conda version : 24.1.2
conda-build version : 24.1.2
python version : 3.11.7.final.0
solver : libmamba (default)
virtual packages : __archspec=1=x86_64
__conda=24.1.2=0
__cuda=12.3=0
__win=0=0
base environment : F:\Anaconda (read only)
conda av data dir : F:\Anaconda\etc\conda
conda av metadata url : None
channel URLs : https://repo.anaconda.com/pkgs/main/win-64
https://repo.anaconda.com/pkgs/main/noarch
https://repo.anaconda.com/pkgs/r/win-64
https://repo.anaconda.com/pkgs/r/noarch
https://repo.anaconda.com/pkgs/msys2/win-64
https://repo.anaconda.com/pkgs/msys2/noarch
package cache : F:\Anaconda\pkgs
C:\Users\11043\.conda\pkgs
C:\Users\11043\AppData\Local\conda\conda\pkgs
envs directories : C:\Users\11043\.conda\envs
F:\Anaconda\envs
C:\Users\11043\AppData\Local\conda\conda\envs
platform : win-64
user-agent : conda/24.1.2 requests/2.31.0 CPython/3.11.7 Windows/10 Windows/10.0.22631 solver/libmamba conda-libmamba-solver/24.1.0 libmambapy/1.5.6 aau/0.4.3 c/VZAbQE--iNbp2n9VDN0GPQ s/RRYVJsYFGmMR0XKsAo2GOA
administrator : False
netrc file : None
offline mode : False下面我们来输入一个指令来创建python3.7的环境:conda create -n python37 python=3.7
(base) C:\Users\11043>conda create -n python37 python=3.7
Channels:
- defaults
Platform: win-64
Collecting package metadata (repodata.json): done
Solving environment: done
## Package Plan ##
environment location: C:\Users\11043\.conda\envs\python37
added / updated specs:
- python=3.7
The following packages will be downloaded:
package | build
---------------------------|-----------------
ca-certificates-2024.3.11 | haa95532_0 128 KB
certifi-2022.12.7 | py37haa95532_0 149 KB
openssl-1.1.1w | h2bbff1b_0 5.5 MB
pip-22.3.1 | py37haa95532_0 2.7 MB
python-3.7.16 | h6244533_0 17.2 MB
setuptools-65.6.3 | py37haa95532_0 1.1 MB
sqlite-3.45.3 | h2bbff1b_0 973 KB
wheel-0.38.4 | py37haa95532_0 82 KB
wincertstore-0.2 | py37haa95532_2 15 KB
------------------------------------------------------------
Total: 27.9 MB
The following NEW packages will be INSTALLED:
ca-certificates pkgs/main/win-64::ca-certificates-2024.3.11-haa95532_0
certifi pkgs/main/win-64::certifi-2022.12.7-py37haa95532_0
openssl pkgs/main/win-64::openssl-1.1.1w-h2bbff1b_0
pip pkgs/main/win-64::pip-22.3.1-py37haa95532_0
python pkgs/main/win-64::python-3.7.16-h6244533_0
setuptools pkgs/main/win-64::setuptools-65.6.3-py37haa95532_0
sqlite pkgs/main/win-64::sqlite-3.45.3-h2bbff1b_0
vc pkgs/main/win-64::vc-14.2-h21ff451_1
vs2015_runtime pkgs/main/win-64::vs2015_runtime-14.27.29016-h5e58377_2
wheel pkgs/main/win-64::wheel-0.38.4-py37haa95532_0
wincertstore pkgs/main/win-64::wincertstore-0.2-py37haa95532_2
Proceed ([y]/n)? y
Downloading and Extracting Packages:
Preparing transaction: done
Verifying transaction: done
Executing transaction: done
#
# To activate this environment, use
#
# $ conda activate python37
#
# To deactivate an active environment, use
#
# $ conda deactivate同样,我们略微更改一下指令,也可以安装python3.8:conda create -n python38 python=3.8
完成python环境的安装之后我们就可以使用该环境了
在新安装的python环境中安装Frida
我们可以通过使用以下指令在anaconda终端将环境切换到python3.7:conda activate python37
在此之后我们就可以在python3.7中安装frida了,输入pip install frida==12.8.0:
(python37) C:\Users\11043>pip install frida==12.8.0
Looking in indexes: https://mirrors.aliyun.com/pypi/simple/
Collecting frida==12.8.0
Downloading https://mirrors.aliyun.com/pypi/packages/38/1b/8a462787cedda36c57227ed0babbd80c4c4cc5bc9c1f9b5aa285ed6aebba/frida-12.8.0.tar.gz (6.9 kB)
Preparing metadata (setup.py) ... done
Building wheels for collected packages: frida
Building wheel for frida (setup.py) ... done
Created wheel for frida: filename=frida-12.8.0-cp37-cp37m-win_amd64.whl size=16765861 sha256=9f60e1b1f00e7098ba3eb3997eb3f935c36fe6f7df005e620d934d2b9d31392c
Stored in directory: c:\users\11043\appdata\local\pip\cache\wheels\c7\d7\b2\52787d5207a4fd6bffc3531f61a7077b3fb91f95298b575a21
Successfully built frida
Installing collected packages: frida
Successfully installed frida-12.8.0在终端的开头我们可以看见(base)变成了(python37),若我们想要返回原本的环境,则输入conda activate base就可以了
我们再安装frida-tools,输入pip install frida-tools==5.4.0,这个指令会自动安装Frida的全系列版本产品:
(python37) C:\Users\11043>pip install frida-tools==5.4.0
Looking in indexes: https://mirrors.aliyun.com/pypi/simple/
Collecting frida-tools==5.4.0
Downloading https://mirrors.aliyun.com/pypi/packages/6c/ed/0541eb716815fedc1788e276aeb650a4fd27d17e5393c54de0be3a6373b3/frida-tools-5.4.0.tar.gz (28 kB)
Preparing metadata (setup.py) ... done
Collecting colorama<1.0.0,>=0.2.7
Downloading https://mirrors.aliyun.com/pypi/packages/d1/d6/3965ed04c63042e047cb6a3e6ed1a63a35087b6a609aa3a15ed8ac56c221/colorama-0.4.6-py2.py3-none-any.whl (25 kB)
Requirement already satisfied: frida<13.0.0,>=12.7.3 in c:\users\11043\.conda\envs\python37\lib\site-packages (from frida-tools==5.4.0) (12.8.0)
Collecting prompt-toolkit<3.0.0,>=2.0.0
Downloading https://mirrors.aliyun.com/pypi/packages/87/61/2dfea88583d5454e3a64f9308a686071d58d59a55db638268a6413e1eb6d/prompt_toolkit-2.0.10-py3-none-any.whl (340 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 340.0/340.0 kB 3.0 MB/s eta 0:00:00
Collecting pygments<3.0.0,>=2.0.2
Downloading https://mirrors.aliyun.com/pypi/packages/97/9c/372fef8377a6e340b1704768d20daaded98bf13282b5327beb2e2fe2c7ef/pygments-2.17.2-py3-none-any.whl (1.2 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 1.2/1.2 MB 3.4 MB/s eta 0:00:00
Collecting wcwidth
Downloading https://mirrors.aliyun.com/pypi/packages/fd/84/fd2ba7aafacbad3c4201d395674fc6348826569da3c0937e75505ead3528/wcwidth-0.2.13-py2.py3-none-any.whl (34 kB)
Collecting six>=1.9.0
Downloading https://mirrors.aliyun.com/pypi/packages/d9/5a/e7c31adbe875f2abbb91bd84cf2dc52d792b5a01506781dbcf25c91daf11/six-1.16.0-py2.py3-none-any.whl (11 kB)
Building wheels for collected packages: frida-tools
Building wheel for frida-tools (setup.py) ... done
Created wheel for frida-tools: filename=frida_tools-5.4.0-py3-none-any.whl size=32056 sha256=f27841ebe95a0490b88b90b0c24c97cf3349c0bf734339f071476295673d8ccc
Stored in directory: c:\users\11043\appdata\local\pip\cache\wheels\1f\52\df\750cf2dd60711ca0df70a88204ed2daca4a67cf5eb099482d9
Successfully built frida-tools
Installing collected packages: wcwidth, six, pygments, colorama, prompt-toolkit, frida-tools
Successfully installed colorama-0.4.6 frida-tools-5.4.0 prompt-toolkit-2.0.10 pygments-2.17.2 six-1.16.0 wcwidth-0.2.13再输入pip install objection==1.8.4:
Looking in indexes: https://mirrors.aliyun.com/pypi/simple/
Collecting objection==1.8.4
Downloading https://mirrors.aliyun.com/pypi/packages/33/40/d36e7f877bc8112a54c72363ee54668d633936061465a24f10c455f4e8a4/objection-1.8.4.tar.gz (223 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 223.6/223.6 kB 1.7 MB/s eta 0:00:00
Preparing metadata (setup.py) ... done
Requirement already satisfied: frida in c:\users\11043\.conda\envs\python37\lib\site-packages (from objection==1.8.4) (12.8.0)
Requirement already satisfied: frida-tools<6.0.0 in c:\users\11043\.conda\envs\python37\lib\site-packages (from objection==1.8.4) (5.4.0)
Requirement already satisfied: prompt_toolkit<3.0.0,>=2.0.9 in c:\users\11043\.conda\envs\python37\lib\site-packages (from objection==1.8.4) (2.0.10)
Collecting click
Downloading https://mirrors.aliyun.com/pypi/packages/00/2e/d53fa4befbf2cfa713304affc7ca780ce4fc1fd8710527771b58311a3229/click-8.1.7-py3-none-any.whl (97 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 97.9/97.9 kB ? eta 0:00:00
Collecting tabulate
Downloading https://mirrors.aliyun.com/pypi/packages/40/44/4a5f08c96eb108af5cb50b41f76142f0afa346dfa99d5296fe7202a11854/tabulate-0.9.0-py3-none-any.whl (35 kB)
Collecting delegator.py
Downloading https://mirrors.aliyun.com/pypi/packages/a7/c2/2860c52ef858c4672b6cf637f473e9139342cdb281135db9b3c32cfb0a85/delegator.py-0.1.1-py2.py3-none-any.whl (5.0 kB)
Collecting requests
Downloading https://mirrors.aliyun.com/pypi/packages/70/8e/0e2d847013cb52cd35b38c009bb167a1a26b2ce6cd6965bf26b47bc0bf44/requests-2.31.0-py3-none-any.whl (62 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 62.6/62.6 kB ? eta 0:00:00
Collecting flask
Downloading https://mirrors.aliyun.com/pypi/packages/9f/1a/8b6d48162861009d1e017a9740431c78d860809773b66cac220a11aa3310/Flask-2.2.5-py3-none-any.whl (101 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 101.8/101.8 kB 5.7 MB/s eta 0:00:00
Requirement already satisfied: pygments in c:\users\11043\.conda\envs\python37\lib\site-packages (from objection==1.8.4) (2.17.2)
Collecting litecli==1.1.0
Downloading https://mirrors.aliyun.com/pypi/packages/04/4c/b375b33afe4413cd0eabfc55514f1f4223d0cb0bc44883bb4fd36c982ebb/litecli-1.1.0-py2.py3-none-any.whl (46 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 46.8/46.8 kB 1.2 MB/s eta 0:00:00
Collecting cli-helpers[styles]>=1.0.1
Downloading https://mirrors.aliyun.com/pypi/packages/f1/c5/2deaab90ce50f2e92aaff6e80c4e06a7160f97ae03a3835ae9121a54b428/cli_helpers-2.3.1-py3-none-any.whl (19 kB)
Collecting configobj>=5.0.5
Downloading https://mirrors.aliyun.com/pypi/packages/d3/bb/d10e531b297dd1d46f6b1fd11d018247af9f2d460037554bb7bb9011c6ac/configobj-5.0.8-py2.py3-none-any.whl (36 kB)
Collecting sqlparse<0.3.0,>=0.2.2
Downloading https://mirrors.aliyun.com/pypi/packages/65/85/20bdd72f4537cf2c4d5d005368d502b2f464ede22982e724a82c86268eda/sqlparse-0.2.4-py2.py3-none-any.whl (38 kB)
Collecting importlib-metadata
Downloading https://mirrors.aliyun.com/pypi/packages/ff/94/64287b38c7de4c90683630338cf28f129decbba0a44f0c6db35a873c73c4/importlib_metadata-6.7.0-py3-none-any.whl (22 kB)
Requirement already satisfied: colorama in c:\users\11043\.conda\envs\python37\lib\site-packages (from click->objection==1.8.4) (0.4.6)
Requirement already satisfied: six>=1.9.0 in c:\users\11043\.conda\envs\python37\lib\site-packages (from prompt_toolkit<3.0.0,>=2.0.9->objection==1.8.4) (1.16.0)
Requirement already satisfied: wcwidth in c:\users\11043\.conda\envs\python37\lib\site-packages (from prompt_toolkit<3.0.0,>=2.0.9->objection==1.8.4) (0.2.13)
Collecting pexpect>=4.1.0
Downloading https://mirrors.aliyun.com/pypi/packages/9e/c3/059298687310d527a58bb01f3b1965787ee3b40dce76752eda8b44e9a2c5/pexpect-4.9.0-py2.py3-none-any.whl (63 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 63.8/63.8 kB ? eta 0:00:00
Collecting Werkzeug>=2.2.2
Downloading https://mirrors.aliyun.com/pypi/packages/f6/f8/9da63c1617ae2a1dec2fbf6412f3a0cfe9d4ce029eccbda6e1e4258ca45f/Werkzeug-2.2.3-py3-none-any.whl (233 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 233.6/233.6 kB 4.9 MB/s eta 0:00:00
Collecting itsdangerous>=2.0
Downloading https://mirrors.aliyun.com/pypi/packages/68/5f/447e04e828f47465eeab35b5d408b7ebaaaee207f48b7136c5a7267a30ae/itsdangerous-2.1.2-py3-none-any.whl (15 kB)
Collecting Jinja2>=3.0
Downloading https://mirrors.aliyun.com/pypi/packages/31/80/3a54838c3fb461f6fec263ebf3a3a41771bd05190238de3486aae8540c36/jinja2-3.1.4-py3-none-any.whl (133 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 133.3/133.3 kB 8.2 MB/s eta 0:00:00
Collecting charset-normalizer<4,>=2
Downloading https://mirrors.aliyun.com/pypi/packages/96/fc/0cae31c0f150cd1205a2a208079de865f69a8fd052a98856c40c99e36b3c/charset_normalizer-3.3.2-cp37-cp37m-win_amd64.whl (98 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 98.1/98.1 kB ? eta 0:00:00
Requirement already satisfied: certifi>=2017.4.17 in c:\users\11043\.conda\envs\python37\lib\site-packages (from requests->objection==1.8.4) (2022.12.7)
Collecting idna<4,>=2.5
Downloading https://mirrors.aliyun.com/pypi/packages/e5/3e/741d8c82801c347547f8a2a06aa57dbb1992be9e948df2ea0eda2c8b79e8/idna-3.7-py3-none-any.whl (66 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 66.8/66.8 kB ? eta 0:00:00
Collecting urllib3<3,>=1.21.1
Downloading https://mirrors.aliyun.com/pypi/packages/d2/b2/b157855192a68541a91ba7b2bbcb91f1b4faa51f8bae38d8005c034be524/urllib3-2.0.7-py3-none-any.whl (124 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 124.2/124.2 kB 7.6 MB/s eta 0:00:00
Collecting typing-extensions>=3.6.4
Downloading https://mirrors.aliyun.com/pypi/packages/ec/6b/63cc3df74987c36fe26157ee12e09e8f9db4de771e0f3404263117e75b95/typing_extensions-4.7.1-py3-none-any.whl (33 kB)
Collecting zipp>=0.5
Downloading https://mirrors.aliyun.com/pypi/packages/5b/fa/c9e82bbe1af6266adf08afb563905eb87cab83fde00a0a08963510621047/zipp-3.15.0-py3-none-any.whl (6.8 kB)
Collecting MarkupSafe>=2.0
Downloading https://mirrors.aliyun.com/pypi/packages/6c/4c/3577a52eea1880538c435176bc85e5b3379b7ab442327ccd82118550758f/MarkupSafe-2.1.5-cp37-cp37m-win_amd64.whl (17 kB)
Collecting ptyprocess>=0.5
Downloading https://mirrors.aliyun.com/pypi/packages/22/a6/858897256d0deac81a172289110f31629fc4cee19b6f01283303e18c8db3/ptyprocess-0.7.0-py2.py3-none-any.whl (13 kB)
Building wheels for collected packages: objection
Building wheel for objection (setup.py) ... done
Created wheel for objection: filename=objection-1.8.4-py3-none-any.whl size=286310 sha256=bef993a5aa8554f2cf52c5d00b75b9d3c33d482c4743ba81580ec068c9f63122
Stored in directory: c:\users\11043\appdata\local\pip\cache\wheels\fc\7e\cf\af9ead29c2ac430224467cccf15d3acb3ff664c1dee35d0c40
Successfully built objection
Installing collected packages: sqlparse, ptyprocess, zipp, urllib3, typing-extensions, tabulate, pexpect, MarkupSafe, itsdangerous, idna, configobj, charset-normalizer, Werkzeug, requests, Jinja2, importlib-metadata, delegator.py, click, cli-helpers, flask, litecli, objection
Successfully installed Jinja2-3.1.4 MarkupSafe-2.1.5 Werkzeug-2.2.3 charset-normalizer-3.3.2 cli-helpers-2.3.1 click-8.1.7 configobj-5.0.8 delegator.py-0.1.1 flask-2.2.5 idna-3.7 importlib-metadata-6.7.0 itsdangerous-2.1.2 litecli-1.1.0 objection-1.8.4 pexpect-4.9.0 ptyprocess-0.7.0 requests-2.31.0 sqlparse-0.2.4 tabulate-0.9.0 typing-extensions-4.7.1 urllib3-2.0.7 zipp-3.15.0可以输入检查版本信息的指令查看是否安装成功:
(python37) C:\Users\11043>objection version
objection: 1.8.4
(python37) C:\Users\11043>frida --version
12.8.0安装frida-server
由于我们并不是对本机的程序使用frida进行hook,所以仅仅在计算机上安装Frida是不够的,我们还需要在对应的模拟器/真机上安装对应的server。其中有几个需要注意的点,一是frida-server的版本需要与计算机上的frida版本一致,比如说上文我们安装的是12.8.0版本的frida,则frida-server也需要安装对应的版本;二是frida-server的架构需要与模拟器/真机上的系统以及架构一致,通常我们可以在adb shell中输入getprop ro.product.cpu.abi查看手机架构:
C:\Users\11043>adb shell
root@aosp:/ # getprop ro.product.cpu.abi
x86在上文调试.so文件时也提到过如何查看架构,接下来我们需要做的就是下载server并push到模拟器里面去,进入frida的github其中的release:下载对应的Frida 12.8.0
这里下载下来的server是.xz的,我们需要先解压再将其push到模拟器上:
上述报错是由于x86和arm不兼容导致的,不用理会,不影响我们进行逆向调试:
【Android 逆向】Frida 框架 ( Frida 2 种运行模式 | Frida 12.7.5 版本相关工具下载地址 | 在 Android 模拟器上运行 Frida 远程服务程序 )51CTO博客_Android frida
进入并启动frida-objection,hook函数
在模拟器上完成server的运行之后,我们就可以回到Anaconda的python环境中了
(base) C:\Users\11043>conda activate python37
(python37) C:\Users\11043>frida version
____
/ _ | Frida 12.8.0 - A world-class dynamic instrumentation toolkit
| (_| |
> _ | Commands:
/_/ |_| help -> Displays the help system
. . . . object? -> Display information about 'object'
. . . . exit/quit -> Exit
. . . .
. . . . More info at https://www.frida.re/docs/home/
Failed to spawn: unable to find process with name 'version'
(python37) C:\Users\11043>objection version
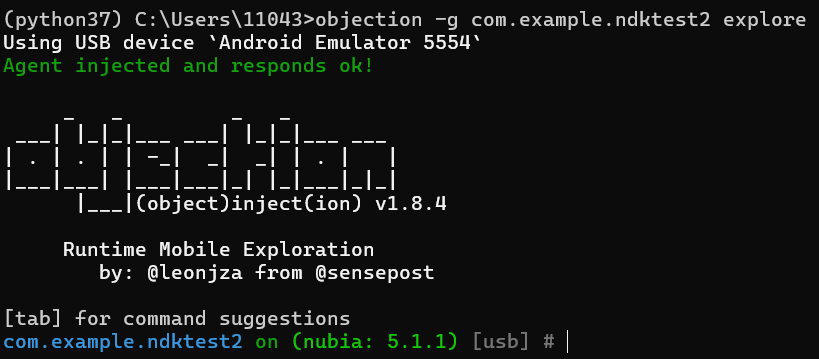
objection: 1.8.4启动objection注入objection -g com.example.ndktest2 explore:
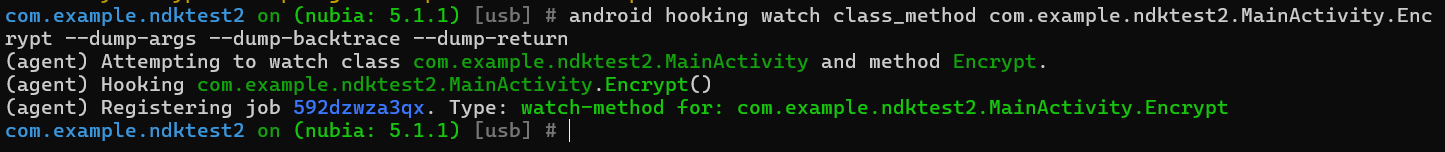
启动之后我们输入android hooking watch class_method com.example.ndktest2.MainActivity.Encrypt --dump-args --dump-backtrace --dump-return启动hook:
再回到objection就会发现hook到的返回值已经给出来了:
再次输入返回的结果,就会显示登陆成功了




师傅,想问一下,安装frida时候怎么搞的
pip install frida==12.8.0
WARNING: Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘ProxyError(‘Cannot connect to proxy.’, OSError(0, ‘Error’))’: /simple/frida/
WARNING: Retrying (Retry(total=3, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘ProxyError(‘Cannot connect to proxy.’, OSError(0, ‘Error’))’: /simple/frida/
WARNING: Retrying (Retry(total=2, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘ProxyError(‘Cannot connect to proxy.’, OSError(0, ‘Error’))’: /simple/frida/
WARNING: Retrying (Retry(total=1, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘ProxyError(‘Cannot connect to proxy.’, OSError(0, ‘Error’))’: /simple/frida/
WARNING: Retrying (Retry(total=0, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘ProxyError(‘Cannot connect to proxy.’, OSError(0, ‘Error’))’: /simple/frida/
ERROR: Could not find a version that satisfies the requirement frida==12.8.0 (from versions: none)
ERROR: No matching distribution found for frida==12.8.0
WARNING: There was an error checking the latest version of pip.
换成国内的源应该就好了,或者你可以挂个梯子
挂着呢,换源也试过还是不行,好像是说 pip 的版本太低